RFI Global acquires DBM’s Atlas division, to create Australia’s most comprehensive financial services customer data set. Read the press release.
Intelligence To Bank On
RFI Global is trusted by leaders in the financial services industry to deliver tailored market research insights to catalyse product innovation, enhance customer experience, and grow market share.










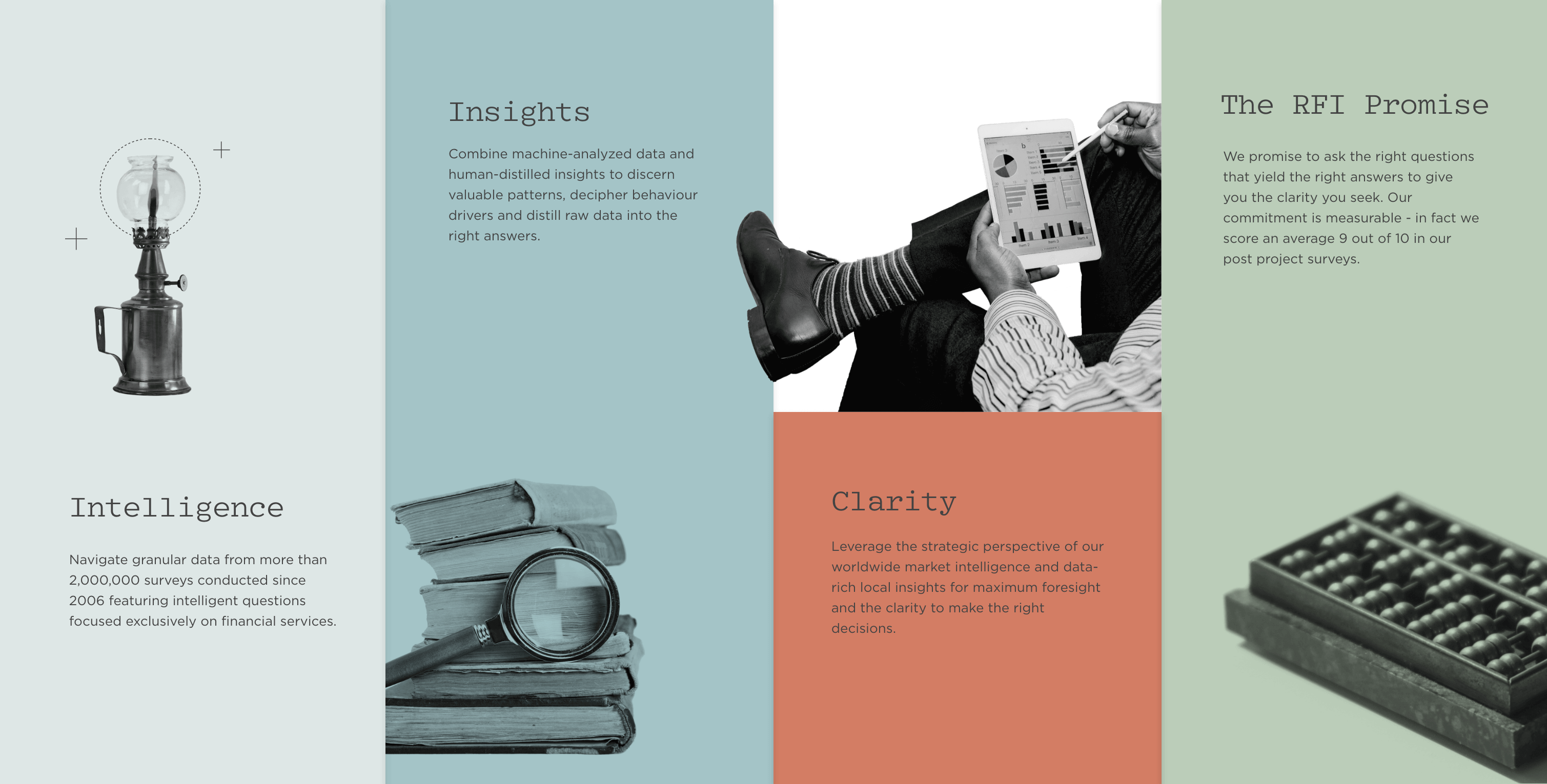
Our Commitment is Measurable
How can you be sure we will deliver actionable insights? This is where RFI Promise comes in:
"We promise to provide data-driven actionable insights and recommendations that answer your business questions".

Keep your finger on the pulse and stay up to date with
our latest data and insights as they come out of the field.
Loud Budgeting and the Big Switch
21 Feb 2024 \ Budgeting
Avoiding the ‘Intergenerational Tragedy’
28 Nov 2023
The Rise of Mobile Wallets in Canada
14 Sep 2023 \ Payments








































/NQA-ISO-27001-Logo-UKAS.jpg)